The ascent of secure application advancement has put OpenZiti at the front of zero-trust organizing arrangements. OpenZiti’s C-SDK furnishes engineers with vigorous instruments to make applications that guarantee secure, consistent correspondence. This guide jumps into dominating the OpenZiti C-SDK, with a unique spotlight on executing Multifaceted Verification (MFA). Whether you’re an understudy or a carefully prepared engineer, this article will give significant experiences and useful moves toward upgrade your improvement process.
What is OpenZiti C-SDK?

OpenZiti’s C-SDK is a Product Improvement Pack that enables engineers to insert zero-trust network abilities straightforwardly into their applications. By utilizing the C-SDK, designers can make secure, dependable, and adaptable applications without depending on conventional Virtual Confidential Organizations (VPNs).
Also Check: How Mann C 3459 Cross Reference Simplifies Car Repairs
Key Features of OpenZiti C-SDK:
- Zero-Trust Security: Ensures only authenticated users and devices can access applications.
- Direct Application Embedding: Adds secure networking capabilities without altering existing infrastructure.
- Flexibility: Compatible with various operating systems and environments.
- Scalability: Handles enterprise-level applications with ease.
Setting Up the OpenZiti C-SDK
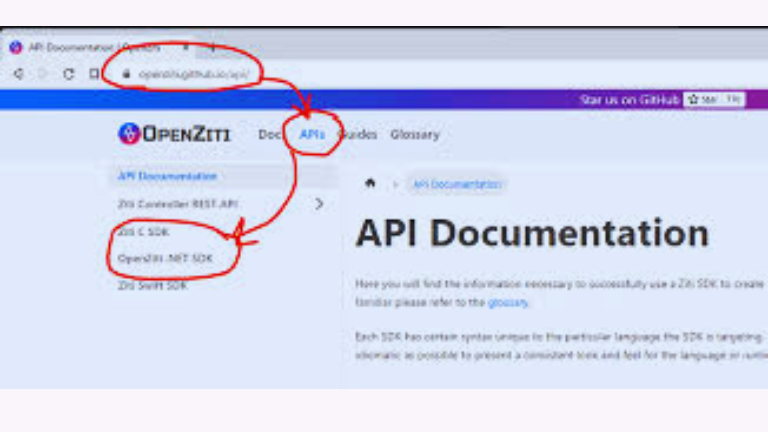
Before diving into MFA integration, it is essential to set up the OpenZiti C-SDK correctly. Follow these steps:
- Install the SDK:
- Clone the repository from OpenZiti GitHub.
- Follow the installation instructions to build the SDK on your system.
- Configure Your Environment:
- Set up Ziti Edge Router and Controller to manage secure connections.
- Generate identity files for authentication.
- Test Basic Connectivity:
- Run the sample applications provided in the repository to ensure the SDK is working correctly.
Understanding Multi-Factor Authentication (MFA)
MFA adds an extra layer of safety by expecting clients to confirm their personality through numerous elements. With regards to OpenZiti, MFA guarantees that just verified and pose consistent characters get close enough to applications.
Why Use MFA?
- Enhanced Security: Protects against unauthorized access.
- Compliance: Meets regulatory requirements for sensitive data.
- User Trust: Boosts user confidence in application security.
Implementing MFA with OpenZiti C-SDK
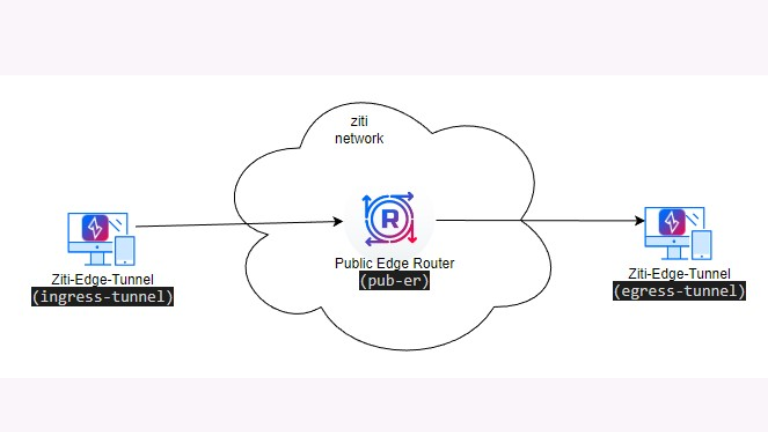
MFA integration with OpenZiti C-SDK involves configuring posture checks, enabling MFA policies, and embedding the necessary logic into your application. Here is a step-by-step guide:
1. Configure MFA Policies in Ziti Controller
- Access the Ziti Controller’s management console.
- Define MFA policies that specify required authentication factors.
- Enable posture checks for devices to ensure compliance.
2. Update the Application’s Identity
- Generate or update the application’s identity file to include MFA requirements.
- Use the Ziti CLI to configure the identity.
3. Integrate MFA in Application Code
- Leverage the C-SDK’s APIs to invoke MFA during user authentication.
- Example code snippet for MFA invocation:
// Example: Invoking MFA using OpenZiti C-SDK ziti_auth_query_mfa_response *mfa_resp; if (ziti_auth_query_mfa(ziti_context, &mfa_resp) == ZITI_OK) { printf("MFA challenge initiated\n"); // Handle MFA response } else { printf("Failed to initiate MFA\n"); }
4. Test the MFA Integration
- Simulate different user scenarios to ensure MFA works as intended.
- Use tools like Postman or curl for API testing.
Common Challenges and Solutions
Challenge 1: Misconfigured Identity Files
- Solution: Double-check the identity JSON file for proper formatting and required attributes.
Challenge 2: Failed Posture Checks
- Solution: Ensure that the device meets all posture requirements defined in the Ziti Controller.
Challenge 3: Debugging Errors
- Solution: Use the verbose logging feature in the C-SDK to identify and fix issues.
Advanced Topics
Integrating with Existing Authentication Systems
- OpenZiti can work alongside traditional authentication systems like OAuth2 or LDAP for enhanced security.
Real-Time Posture Checks
- Enable dynamic posture checks to assess device compliance in real-time.
Extending MFA with Biometrics
- Utilize biometric sensors for additional layers of authentication, ensuring top-tier security.
Best Practices for Using OpenZiti C-SDK
- Keep SDK Updated: Regularly update the SDK to leverage new features and security patches.
- Enable Detailed Logs: Use detailed logging to monitor application performance and security.
- Optimize Code: Minimize overhead by streamlining the MFA workflow.
- Educate Users: Provide clear instructions to users on completing MFA challenges.
Resources and Community Support
For additional support and resources:
Also Check: Why Choose Maxtana Avenue LLC for Your Projects?
FAQs
What is the main benefit of using OpenZiti C-SDK for MFA integration?
The OpenZiti C-SDK simplifies embedding zero-trust networking into applications, offering seamless MFA integration to enhance security and ensure compliance without requiring extensive infrastructure changes.
How do I troubleshoot MFA-related errors during development?
Start by enabling verbose logging in the C-SDK to identify error sources. Verify the configuration of identity files and posture checks in the Ziti Controller, and test the application\u2019s authentication flow with simulated scenarios.
Can I use OpenZiti C-SDK alongside other authentication systems like OAuth2?
Yes, OpenZiti C-SDK is designed to integrate with existing authentication frameworks such as OAuth2 and LDAP, providing an additional security layer with zero-trust principles.
Conclusion
Mastering OpenZiti’s C-SDK and integrating MFA is a critical step toward building secure, zero-trust applications. By following this guide, developers can ensure their applications meet the highest security standards while providing a seamless user experience. With its powerful features and community support, OpenZiti C-SDK makes implementing zero-trust security simpler than ever. Start integrating today and transform your application security practices.

